The world of cryptocurrency is no stranger to headlines about hacks and breaches, but the recent Bybit incident has sent shockwaves across the industry. For those who rely on cold wallets for their digital assets, the $1.4 billion ETH hack serves as a chilling reminder that even the most secure storage solutions can be vulnerable under the right circumstances. But what exactly happened at Bybit, and more importantly, what can we learn from it to safeguard our own holdings? Let’s dive into the story, unpack the complexities of cold wallet security, and explore how to stay one step ahead of hackers.
Contents
- 1 Bybit Reports Cold Wallet Hack: Over $1.5 Billion in ETH Stolen Through Smart Contract Exploit
- 2 What Are Cold Wallets, and Why Are They Not Invincible?
- 3 How Hackers Steal ETH: Lessons from the Bybit Breach
- 4 How to Safeguard Your ETH: Best Practices for Cold Storage
- 5 What Is cmETH, and How Does It Enhance Security?
- 6 Staying Ahead of Hackers: The Role of Vigilance
- 7 Conclusion: Turning Lessons into Action
Bybit Reports Cold Wallet Hack: Over $1.5 Billion in ETH Stolen Through Smart Contract Exploit
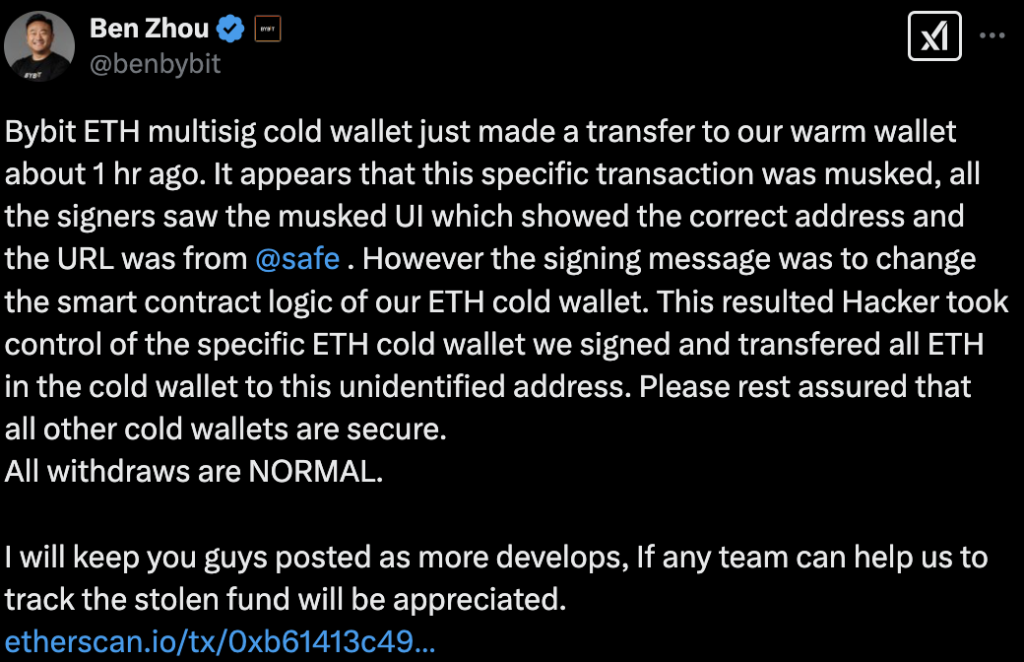
On February 21, 2025, Bybit, a leading crypto exchange, detected unauthorized activity in one of its Ethereum (ETH) cold wallets. The attack was nothing short of sophisticated. Bybit’s ETH multisignature (multisig) cold wallet had executed a transfer to its warm wallet—a standard procedure for exchanges managing liquidity. However, this particular transaction was manipulated in a way that stunned the crypto community.
The attacker employed a highly advanced tactic, masking the signing interface to display the correct wallet address while altering the underlying smart contract logic. This allowed them to bypass the multisig approval process and gain full control of the wallet. In a matter of moments, the hacker transferred $1.4 billion worth of ETH to an unidentified address.
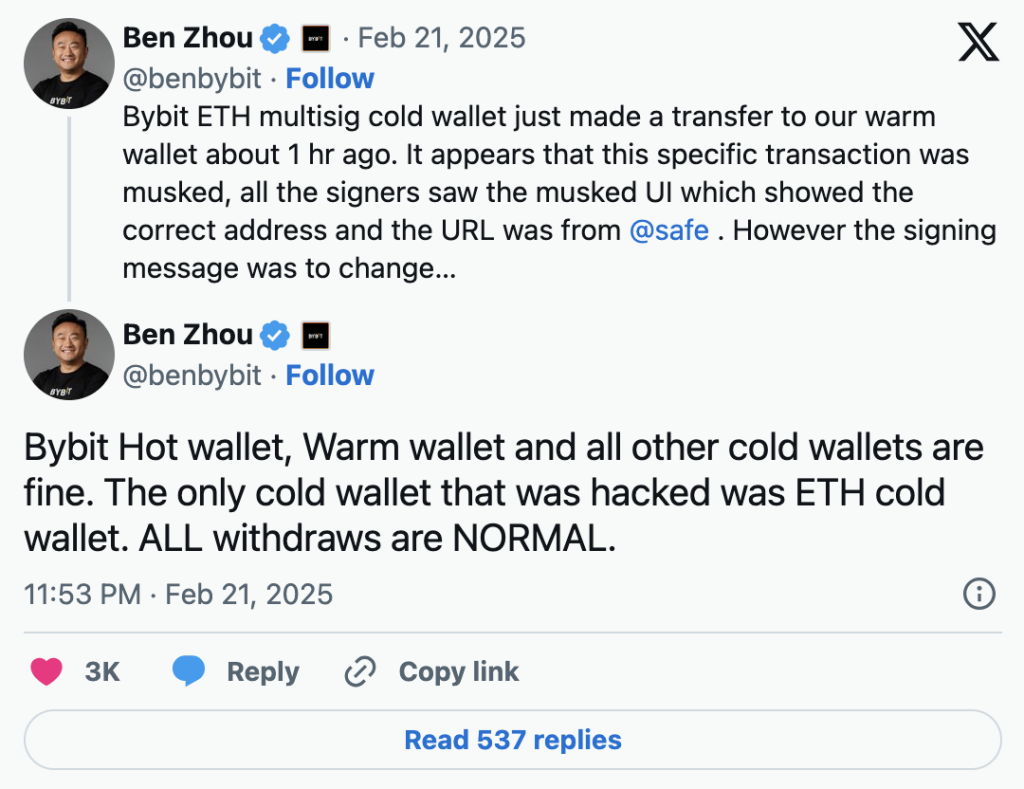
Bybit’s swift response reassured users that all other wallets remained secure and that client funds were unaffected. The exchange also emphasized its solvency, ensuring users that all assets were backed 1:1. While this transparency is commendable, the incident raises crucial questions: How could a cold wallet—considered one of the safest storage methods—be compromised? And what steps can users take to protect their own assets?
What Are Cold Wallets, and Why Are They Not Invincible?
To understand the implications of the Bybit hack, it’s essential to first grasp what a cold wallet is. Cold wallets are offline storage solutions designed to keep cryptocurrencies safe from online threats. Unlike hot wallets, which are connected to the internet and used for frequent transactions, cold wallets are akin to a locked safe—disconnected from the digital world and theoretically immune to hacking attempts.
I’ve written a new article for you about what is cold wallet and what is warm wallet. I hope it helps!
However, as the Bybit case demonstrates, no system is entirely foolproof. Cold wallets rely on specific protocols and interfaces for transactions. In this instance, the attacker exploited the multisig process—a security feature requiring multiple approvals for a transaction. By masking the signing interface, they tricked the wallet’s custodians into approving a malicious transaction.
This highlights a critical point: while cold wallets are incredibly secure, their vulnerabilities often lie in the human or procedural elements surrounding their use. The attack on Bybit wasn’t a failure of the wallet itself but rather a manipulation of the processes designed to protect it.
How Hackers Steal ETH: Lessons from the Bybit Breach
The Bybit hack is a textbook example of how hackers exploit even the most secure systems. By altering the smart contract logic, the attacker effectively rewrote the rules governing the wallet’s behavior. This allowed them to bypass the multisig requirement, gaining control without triggering any alarms.
Such attacks are a stark reminder of the importance of vigilance. Hackers often use methods like phishing, social engineering, and interface manipulation to exploit weaknesses. In Bybit’s case, the masked UI tricked even seasoned professionals into signing off on a fraudulent transaction.
How to Safeguard Your ETH: Best Practices for Cold Storage
So, what can you do to protect your ETH and other digital assets? The Bybit incident underscores the need for a multi-layered approach to security:
- Choose the Right Cold Wallet: Not all cold wallets are created equal. Hardware wallets like Ledger and Trezor are popular choices for individual users, while multisig wallets are often used by institutions.
- Verify Every Transaction: Always double-check wallet addresses and transaction details, especially when using multisig wallets. If possible, use multiple devices to cross-verify information.
- Keep Firmware Updated: Regularly update your wallet’s firmware to patch any security vulnerabilities.
- Use Trusted Interfaces: Ensure that the platforms and interfaces you use are reputable and secure. Avoid clicking on unfamiliar links or downloading unverified software.
What Is cmETH, and How Does It Enhance Security?
In the context of Ethereum, cmETH (collateralized staking ETH) is becoming an increasingly popular option for users looking to earn rewards through staking. By staking ETH, users contribute to the network’s security and earn interest in return. However, staking comes with its own set of risks, including the time required to unstake assets.
Unstaking ETH typically takes several days due to the network’s design, which ensures stability and security. While this delay can be frustrating, it’s a necessary trade-off to prevent malicious actors from destabilizing the network.
Staying Ahead of Hackers: The Role of Vigilance
The Bybit hack serves as a wake-up call for the entire crypto community. Even with robust security measures in place, complacency can be costly. Whether you’re storing ETH in a cold wallet, staking it for rewards, or simply holding it on an exchange, the key to safeguarding your assets lies in constant vigilance.
For exchanges like WEEX, the focus remains on transparency, security, and user education. By learning from incidents like the Bybit breach, both exchanges and users can work together to create a safer crypto ecosystem. Expanding Utility Across the WEEX Ecosystem
WEEX Exchange: A Secure and Transparent Ecosystem Backed by Numbers
Since its launch in August 2023, WXT has seen a cumulative price increase of 384%, reflecting its growing utility and market confidence. Over the past year, WEEX has solidified its presence in the global cryptocurrency market:
Daily Trading Volume: Exceeding $20 billion, consistently ranking among the top 10 derivatives exchanges.
Active User Base: Over 5 million users, supported by partnerships with 10000 star traders and 2000 global influencers.
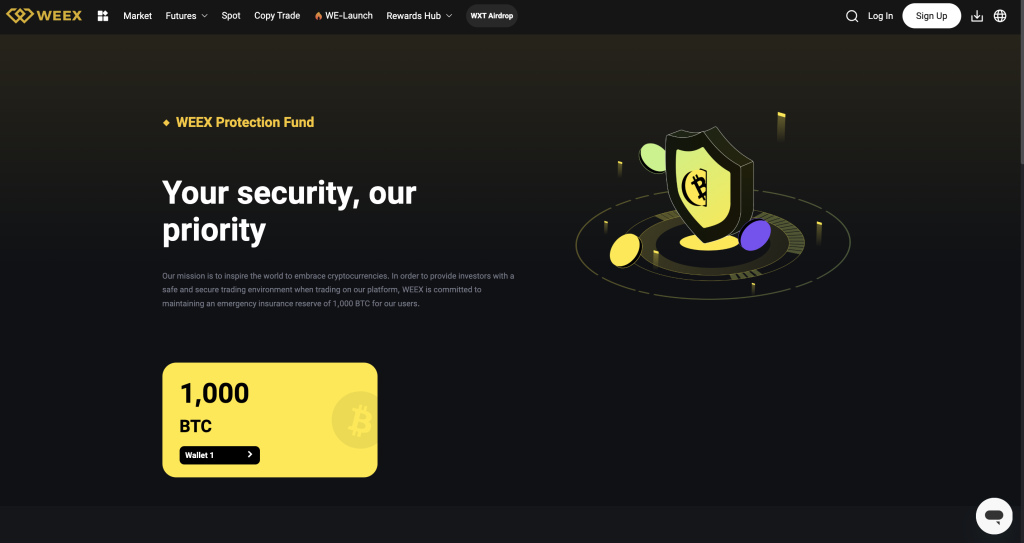
Security and Transparency: Backed by a 1000 BTC investor protection fund and on-chain verification of all token burns.
Conclusion: Turning Lessons into Action
The Bybit hack is a sobering reminder that even the most secure systems are not immune to attack. However, it also provides an opportunity to learn and improve. By understanding the vulnerabilities of cold wallets, adopting best practices for ETH storage, and staying informed about emerging threats, users can take proactive steps to protect their assets.
As the crypto industry continues to evolve, one thing is clear: security is a shared responsibility. By staying vigilant and working together, we can build a future where incidents like the Bybit hack become a thing of the past.
At WEEX, you can trade BTC USDT, ETH USDT, PI USDT, and WXT USDT with lower trading fees. New users can earn over 100 USDT in rewards. It’s a secure and reliable exchange you won’t want to miss!

